| | 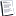 'TR/Crypt.XPACK.Gen2' und 'Trojan.W32.Grumm ALARM' gefunden in C:\documents and setti
sorry dass das ding so hartnäckig is Zitat:
AVZ Antiviral Toolkit log; AVZ version is 4.32
Scanning started at 29.04.2010 23:43:09
Database loaded: signatures - 271306, NN profile(s) - 2, malware removal microprograms - 56, signature database released 28.04.2010 23:12
Heuristic microprograms loaded: 383
PVS microprograms loaded: 9
Digital signatures of system files loaded: 198521
Heuristic analyzer mode: Medium heuristics mode
Malware removal mode: disabled
Windows version is: 5.1.2600, Service Pack 3 ; AVZ is run with administrator rights
System Restore: enabled
1. Searching for Rootkits and other software intercepting API functions
1.1 Searching for user-mode API hooks
Analysis: kernel32.dll, export table found in section .text
Analysis: ntdll.dll, export table found in section .text
Analysis: user32.dll, export table found in section .text
Analysis: advapi32.dll, export table found in section .text
Analysis: ws2_32.dll, export table found in section .text
Analysis: wininet.dll, export table found in section .text
Analysis: rasapi32.dll, export table found in section .text
Analysis: urlmon.dll, export table found in section .text
Analysis: netapi32.dll, export table found in section .text
1.2 Searching for kernel-mode API hooks
Driver loaded successfully
SDT found (RVA=085700)
Kernel ntkrnlpa.exe found in memory at address 804D7000
SDT = 8055C700
KiST = 8050446C (284)
Function NtClose (19) intercepted (805BC4DC->A869188E), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtCreateFile (25) intercepted (80579084->A86910EC), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtCreateKey (29) intercepted (806237C8->A8690DCE), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtCreateSection (32) intercepted (805AB38E->A8692938), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtCreateThread (35) intercepted (805D0FD2->BA7A8C4C), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtDeleteKey (3F) intercepted (80623C64->A8690ED8), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtDeleteValueKey (41) intercepted (80623E34->A8690FC2), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtLoadDriver (61) intercepted (8058413A->A8691BBC), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtLoadKey (62) intercepted (806259EC->BA7A8C6A), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtOpenFile (74) intercepted (8057A182->A86913F4), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtOpenProcess (7A) intercepted (805CB3FA->BA7A8C38), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtOpenThread (80) intercepted (805CB686->BA7A8C3D), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtReplaceKey (C1) intercepted (8062589C->BA7A8C74), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtRestoreKey (CC) intercepted (806251A8->BA7A8C6F), hook not defined
>>> Function restored successfully !
>>> Hook code blocked
Function NtSetInformationFile (E0) intercepted (8057B010->A8691526), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtSetValueKey (F7) intercepted (80621D3A->A8690BFC), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtTerminateProcess (101) intercepted (805D2982->A8691B04), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Function NtWriteFile (112) intercepted (8057CEF2->A869170C), hook C:\WINDOWS\system32\drivers\sp_rsdrv2.sys, driver recognized as trusted
>>> Function restored successfully !
>>> Hook code blocked
Functions checked: 284, intercepted: 18, restored: 18
1.3 Checking IDT and SYSENTER
Analyzing CPU 1
Analyzing CPU 2
CmpCallCallBacks = 00093D84
Disable callback OK
Checking IDT and SYSENTER - complete
1.4 Searching for masking processes and drivers
Checking not performed: extended monitoring driver (AVZPM) is not installed
Driver loaded successfully
1.5 Checking IRP handlers
Checking - complete
2. Scanning RAM
Number of processes found: 39
Number of modules loaded: 379
Scanning RAM - complete
3. Scanning disks
Direct reading: C:\Documents and Settings\Australia\Cookies\index.dat
Direct reading: C:\Documents and Settings\Australia\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
Direct reading: C:\Documents and Settings\Australia\Local Settings\History\History.IE5\index.dat
Direct reading: C:\Documents and Settings\Australia\Local Settings\Temporary Internet Files\Content.IE5\index.dat
Direct reading: C:\Documents and Settings\Australia\NTUSER.DAT
Direct reading: C:\Documents and Settings\LocalService\Cookies\index.dat
Direct reading: C:\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
Direct reading: C:\Documents and Settings\LocalService\Local Settings\History\History.IE5\index.dat
Direct reading: C:\Documents and Settings\LocalService\Local Settings\Temporary Internet Files\Content.IE5\index.dat
Direct reading: C:\Documents and Settings\LocalService\NTUSER.DAT
Direct reading: C:\Documents and Settings\NetworkService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
Direct reading: C:\Documents and Settings\NetworkService\NTUSER.DAT
Direct reading: C:\Program Files\ASUS\Eee Storage\client.db
C:\Program Files\Common Files\Windows Live\.cache\a33ab1e21c9928f\fssclient_x86.msi/{MS-OLE}/\8 >>>>> Trojan.Kyjak
Direct reading: C:\System Volume Information\_restore{9A8724D7-8B67-4B8F-808E-B2593C802BA3}\RP141\change.log
Direct reading: C:\WINDOWS\SchedLgU.Txt
Direct reading: C:\WINDOWS\SoftwareDistribution\ReportingEvents.log
Direct reading: C:\WINDOWS\system32\CatRoot2\edb.log
Direct reading: C:\WINDOWS\system32\CatRoot2\tmp.edb
Direct reading: C:\WINDOWS\system32\config\AppEvent.Evt
Direct reading: C:\WINDOWS\system32\config\default
Direct reading: C:\WINDOWS\system32\config\Internet.evt
Direct reading: C:\WINDOWS\system32\config\ODiag.evt
Direct reading: C:\WINDOWS\system32\config\OSession.evt
Direct reading: C:\WINDOWS\system32\config\SAM
Direct reading: C:\WINDOWS\system32\config\SecEvent.Evt
Direct reading: C:\WINDOWS\system32\config\SECURITY
Direct reading: C:\WINDOWS\system32\config\SysEvent.Evt
Direct reading: C:\WINDOWS\system32\config\system
Direct reading: C:\WINDOWS\system32\wbem\Repository\FS\INDEX.BTR
Direct reading: C:\WINDOWS\system32\wbem\Repository\FS\OBJECTS.DATA
Direct reading: C:\WINDOWS\Temp\Perflib_Perfdata_6e8.dat
Direct reading: C:\WINDOWS\WindowsUpdate.log
4. Checking Winsock Layered Service Provider (SPI/LSP)
LSP settings checked. No errors detected
5. Searching for keyboard/mouse/windows events hooks (Keyloggers, Trojan DLLs)
6. Searching for opened TCP/UDP ports used by malicious software
Checking - disabled by user
7. Heuristic system check
Checking - complete
8. Searching for vulnerabilities
>> Services: potentially dangerous service allowed: TermService (Terminal Services)
>> Services: potentially dangerous service allowed: SSDPSRV (SSDP Discovery Service)
>> Services: potentially dangerous service allowed: TlntSvr ()
>> Services: potentially dangerous service allowed: Schedule (Task Scheduler)
>> Services: potentially dangerous service allowed: mnmsrvc (NetMeeting Remote Desktop Sharing)
>> Services: potentially dangerous service allowed: RDSessMgr (Remote Desktop Help Session Manager)
> Services: please bear in mind that the set of services depends on the use of the PC (home PC, office PC connected to corporate network, etc)!
>> Security: disk drives' autorun is enabled
>> Security: administrative shares (C$, D$ ...) are enabled
>> Security: anonymous user access is enabled
>> Security: sending Remote Assistant queries is enabled
Checking - complete
9. Troubleshooting wizard
>> HDD autorun is allowed
>> Network drives autorun is allowed
>> Removable media autorun is allowed
Checking - complete
Files scanned: 253471, extracted from archives: 177272, malicious software found 1, suspicions - 0
Scanning finished at 30.04.2010 00:28:46
!!! Attention !!! Restored 18 KiST functions during Anti-Rootkit operation
This may affect execution of certain software, so it is strongly recommended to reboot
Time of scanning: 00:45:39
If you have a suspicion on presence of viruses or questions on the suspected objects,
you can address hxxp://virusinfo.info conference
|
|







 Jo, die Datei bzw. deren Name hat einen schlechten "Ruf" da draußen, deshalb war es mal ganz gut, auf Nummer sicher zu gehen.
Jo, die Datei bzw. deren Name hat einen schlechten "Ruf" da draußen, deshalb war es mal ganz gut, auf Nummer sicher zu gehen. 















