
 |
| |||||||
Plagegeister aller Art und deren Bekämpfung: Bitte hilfe für: BAT/Fake.PrivdangerWindows 7 Wenn Du nicht sicher bist, ob Du dir Malware oder Trojaner eingefangen hast, erstelle hier ein Thema. Ein Experte wird sich mit weiteren Anweisungen melden und Dir helfen die Malware zu entfernen oder Unerwünschte Software zu deinstallieren bzw. zu löschen. Bitte schildere dein Problem so genau wie möglich. Sollte es ein Trojaner oder Viren Problem sein wird ein Experte Dir bei der Beseitigug der Infektion helfen. |
 |
| | #1 |
| | Bitte hilfe für: BAT/Fake.Privdanger Hallo, ich hab mich grad hier im forum angemeldet, und hoffe ihr könnt mir etwas helfen. Ich bin eigentlich ein Laie was sowas betrifft. Heute hab ich mir ein BAT/Fake.Privdanger eingefangen. Nun ich hab mich etwas schlau darüber gemacht und hab versucht mit Smitfraudfix das problem zu lösen da das bei einigen wohl geholfen hat. Also im abgesicherten modus erstmal den log erstellt und eigentlicht nachher gelöscht. Ich dachte das problem sei behoben. Als ich den pc danach im normalen modus wieder hochgefahren habe war der wieder da. Abgesehen davon gibts da noch die meldung :Worm.Win32NetBooster die auch noch erscheint.Hab nun absolut keine ahnung was ich weiterhin machen soll. Ich hoffe ihr könnt mir da weiterhelfen. Hier mein hijack log: Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 02:52:05, on 19.06.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180) Boot mode: Normal Running processes: C:\WINDOWS\System32\smss.exe C:\WINDOWS\system32\winlogon.exe C:\WINDOWS\system32\services.exe C:\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\svchost.exe C:\WINDOWS\System32\svchost.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\LEXBCES.EXE C:\WINDOWS\system32\spoolsv.exe C:\WINDOWS\system32\LEXPPS.EXE C:\Programme\Avira\AntiVir PersonalEdition Classic\avguard.exe C:\WINDOWS\Explorer.EXE C:\Programme\Avira\AntiVir PersonalEdition Classic\sched.exe C:\Programme\Symantec\LiveUpdate\ALUSchedulerSvc.exe C:\WINDOWS\System32\svchost.exe C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe C:\Programme\Gemeinsame Dateien\Microsoft Shared\VS7DEBUG\MDM.EXE C:\Programme\Alcohol Soft\Alcohol 120\StarWind\StarWindServiceAE.exe C:\WINDOWS\RTHDCPL.EXE C:\WINDOWS\system32\LXSUPMON.EXE C:\Programme\D-Tools\daemon.exe C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe C:\Programme\Microsoft IntelliPoint\ipoint.exe C:\Programme\Avira\AntiVir PersonalEdition Classic\avgnt.exe C:\Programme\ATI Technologies\ATI.ACE\Core-Static\MOM.exe C:\WINDOWS\system32\ctfmon.exe C:\Programme\Microsoft IntelliPoint\dpupdchk.exe C:\Programme\Gemeinsame Dateien\InstallShield\UpdateService\isuspm.exe C:\Programme\DAEMON Tools Pro\DTProAgent.exe C:\WINDOWS\system32\wuauclt.exe C:\Programme\ATI Technologies\ATI.ACE\Core-Static\ccc.exe C:\WINDOWS\system32\cmd.exe C:\Programme\Mozilla Firefox\firefox.exe C:\Program Files\Trend Micro\HijackThis\HijackThis.exe R1 - HKCU\Software\Microsoft\Internet Explorer\Main,SearchAssistant = http://search.imesh.com/sidebar.html?src=ssb R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://softwarereferral.com/jump.php?wmid=6010&mid=MjI6Ojg5&lid=2 R3 - URLSearchHook: (no name) - {00A6FAF6-072E-44cf-8957-5838F569A31D} - C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL R3 - URLSearchHook: ICQ Toolbar - {855F3B16-6D32-4fe6-8A56-BBB695989046} - C:\PROGRA~1\ICQTOO~1\toolbaru.dll O2 - BHO: MyWebSearch Search Assistant BHO - {00A6FAF1-072E-44cf-8957-5838F569A31D} - C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL O2 - BHO: XTTBPos00 - {055FD26D-3A88-4e15-963D-DC8493744B1D} - C:\PROGRA~1\ICQTOO~1\toolbaru.dll O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Programme\Adobe\Acrobat 7.0\ActiveX\AcroIEHelper.dll O2 - BHO: (no name) - {7E853D72-626A-48EC-A868-BA8D5E23E045} - (no file) O3 - Toolbar: ICQ Toolbar - {855F3B16-6D32-4fe6-8A56-BBB695989046} - C:\PROGRA~1\ICQTOO~1\toolbaru.dll O3 - Toolbar: vrmdtneg - {460B9C85-61E5-4CB6-A4B2-501DE81C4475} - C:\WINDOWS\vrmdtneg.dll O4 - HKLM\..\Run: [Verknüpfung mit der High Definition Audio-Eigenschaftenseite] HDAShCut.exe O4 - HKLM\..\Run: [RTHDCPL] RTHDCPL.EXE O4 - HKLM\..\Run: [Alcmtr] ALCMTR.EXE O4 - HKLM\..\Run: [NeroFilterCheck] C:\WINDOWS\system32\NeroCheck.exe O4 - HKLM\..\Run: [LXSUPMON] C:\WINDOWS\system32\LXSUPMON.EXE RUN O4 - HKLM\..\Run: [ISUSPM Startup] "C:\Programme\Gemeinsame Dateien\InstallShield\UpdateService\isuspm.exe" -startup O4 - HKLM\..\Run: [ISUSScheduler] "C:\Programme\Gemeinsame Dateien\InstallShield\UpdateService\issch.exe" -start O4 - HKLM\..\Run: [DAEMON Tools-1033] "C:\Programme\D-Tools\daemon.exe" -lang 1033 O4 - HKLM\..\Run: [Symantec PIF AlertEng] "C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe" /a /m "C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\AlertEng.dll" O4 - HKLM\..\Run: [IntelliPoint] "C:\Programme\Microsoft IntelliPoint\ipoint.exe" O4 - HKLM\..\Run: [avgnt] "C:\Programme\Avira\AntiVir PersonalEdition Classic\avgnt.exe" /min O4 - HKLM\..\Run: [StartCCC] "C:\Programme\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe" O4 - HKLM\..\Run: [ATICustomerCare] "C:\Programme\ATI\ATICustomerCare\ATICustomerCare.exe" O4 - HKLM\..\Run: [QuickTime Task] "C:\Programme\QuickTime\QTTask.exe" -atboottime O4 - HKCU\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\ctfmon.exe O4 - HKCU\..\Run: [MsnMsgr] "C:\Programme\MSN Messenger\MsnMsgr.Exe" /background O4 - HKCU\..\Run: [Steam] "C:\Programme\Steam\Steam.exe" -silent O4 - HKCU\..\Run: [ISUSPM] "C:\Programme\Gemeinsame Dateien\InstallShield\UpdateService\isuspm.exe" -scheduler O4 - HKCU\..\Run: [DAEMON Tools Pro Agent] "C:\Programme\DAEMON Tools Pro\DTProAgent.exe" O4 - HKCU\..\Run: [ICQ] "C:\PROGRA~1\ICQ6\ICQ.exe" silent O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'LOKALER DIENST') O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'NETZWERKDIENST') O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'SYSTEM') O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'Default user') O4 - Global Startup: Adobe Reader Speed Launch.lnk = C:\Programme\Adobe\Acrobat 7.0\Reader\reader_sl.exe O8 - Extra context menu item: Nach Microsoft &Excel exportieren - res://C:\PROGRA~1\MICROS~3\OFFICE11\EXCEL.EXE/3000 O9 - Extra button: Recherchieren - {92780B25-18CC-41C8-B9BE-3C9C571A8263} - C:\PROGRA~1\MICROS~3\OFFICE11\REFIEBAR.DLL O9 - Extra button: ICQ Lite - {B863453A-26C3-4e1f-A54D-A2CD196348E9} - C:\Programme\ICQLite\ICQLite.exe (file missing) O9 - Extra 'Tools' menuitem: ICQ Lite - {B863453A-26C3-4e1f-A54D-A2CD196348E9} - C:\Programme\ICQLite\ICQLite.exe (file missing) O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe O9 - Extra button: ICQ6 - {E59EB121-F339-4851-A3BA-FE49C35617C2} - C:\Programme\ICQ6\ICQ.exe O9 - Extra 'Tools' menuitem: ICQ6 - {E59EB121-F339-4851-A3BA-FE49C35617C2} - C:\Programme\ICQ6\ICQ.exe O21 - SSODL: xvorfwbd - {2629C9EB-5E35-4249-A6F9-DB62B9393907} - C:\WINDOWS\xvorfwbd.dll O21 - SSODL: wpvmqosg - {024022B6-AF69-4A6F-99E4-488B7F21DAD9} - C:\WINDOWS\wpvmqosg.dll O23 - Service: AntiVir PersonalEdition Classic Planer (AntiVirScheduler) - Avira GmbH - C:\Programme\Avira\AntiVir PersonalEdition Classic\sched.exe O23 - Service: AntiVir PersonalEdition Classic Guard (AntiVirService) - Avira GmbH - C:\Programme\Avira\AntiVir PersonalEdition Classic\avguard.exe O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - C:\WINDOWS\system32\Ati2evxx.exe O23 - Service: ATI Smart - Unknown owner - C:\WINDOWS\system32\ati2sgag.exe O23 - Service: Automatisches LiveUpdate - Scheduler - Symantec Corporation - C:\Programme\Symantec\LiveUpdate\ALUSchedulerSvc.exe O23 - Service: Symantec Lic NetConnect service (CLTNetCnService) - Unknown owner - C:\Programme\Gemeinsame Dateien\Symantec Shared\ccSvcHst.exe (file missing) O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Programme\Gemeinsame Dateien\InstallShield\Driver\1050\Intel 32\IDriverT.exe O23 - Service: LexBce Server (LexBceS) - Lexmark International, Inc. - C:\WINDOWS\system32\LEXBCES.EXE O23 - Service: LiveUpdate - Symantec Corporation - C:\PROGRA~1\Symantec\LIVEUP~1\LUCOMS~2.EXE O23 - Service: LiveUpdate Notice Service Ex (LiveUpdate Notice Ex) - Unknown owner - C:\Programme\Gemeinsame Dateien\Symantec Shared\ccSvcHst.exe (file missing) O23 - Service: LiveUpdate Notice Service - Symantec Corporation - C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe O23 - Service: PC Tools Auxiliary Service (sdAuxService) - PC Tools - C:\Programme\Spyware Doctor\pctsAuxs.exe O23 - Service: PC Tools Security Service (sdCoreService) - PC Tools - C:\Programme\Spyware Doctor\pctsSvc.exe O23 - Service: StarWind AE Service (StarWindServiceAE) - Rocket Division Software - C:\Programme\Alcohol Soft\Alcohol 120\StarWind\StarWindServiceAE.exe O24 - Desktop Component 0: Privacy Protection - file:///C:\WINDOWS\privacy_danger\index.htm -- End of file - 8338 bytes UND HIER DER SMITFRAUDFIX log SmitFraudFix v2.327 Scan done at 3:07:33,93, 19.06.2008 Run from C:\Dokumente und Einstellungen\Patrick\Desktop\SmitfraudFix OS: Microsoft Windows XP [Version 5.1.2600] - Windows_NT The filesystem type is NTFS Fix run in normal mode »»»»»»»»»»»»»»»»»»»»»»»» Process C:\WINDOWS\System32\smss.exe C:\WINDOWS\system32\winlogon.exe C:\WINDOWS\system32\services.exe C:\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\svchost.exe C:\WINDOWS\System32\svchost.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\LEXBCES.EXE C:\WINDOWS\system32\spoolsv.exe C:\WINDOWS\system32\LEXPPS.EXE C:\Programme\Avira\AntiVir PersonalEdition Classic\avguard.exe C:\WINDOWS\Explorer.EXE C:\Programme\Avira\AntiVir PersonalEdition Classic\sched.exe C:\Programme\Symantec\LiveUpdate\ALUSchedulerSvc.exe C:\WINDOWS\System32\svchost.exe C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe C:\Programme\Gemeinsame Dateien\Microsoft Shared\VS7DEBUG\MDM.EXE C:\Programme\Alcohol Soft\Alcohol 120\StarWind\StarWindServiceAE.exe C:\WINDOWS\RTHDCPL.EXE C:\WINDOWS\system32\LXSUPMON.EXE C:\Programme\D-Tools\daemon.exe C:\Programme\Gemeinsame Dateien\Symantec Shared\PIF\{B8E1DD85-8582-4c61-B58F-2F227FCA9A08}\PIFSvc.exe C:\Programme\Microsoft IntelliPoint\ipoint.exe C:\Programme\Avira\AntiVir PersonalEdition Classic\avgnt.exe C:\Programme\ATI Technologies\ATI.ACE\Core-Static\MOM.exe C:\WINDOWS\system32\ctfmon.exe C:\Programme\Microsoft IntelliPoint\dpupdchk.exe C:\Programme\Gemeinsame Dateien\InstallShield\UpdateService\isuspm.exe C:\Programme\DAEMON Tools Pro\DTProAgent.exe C:\WINDOWS\system32\wuauclt.exe C:\Programme\ATI Technologies\ATI.ACE\Core-Static\ccc.exe C:\WINDOWS\system32\cmd.exe C:\Programme\Mozilla Firefox\firefox.exe C:\Program Files\Trend Micro\HijackThis\HijackThis.exe C:\WINDOWS\system32\NOTEPAD.EXE »»»»»»»»»»»»»»»»»»»»»»»» hosts »»»»»»»»»»»»»»»»»»»»»»»» C:\ »»»»»»»»»»»»»»»»»»»»»»»» C:\WINDOWS »»»»»»»»»»»»»»»»»»»»»»»» C:\WINDOWS\system »»»»»»»»»»»»»»»»»»»»»»»» C:\WINDOWS\Web »»»»»»»»»»»»»»»»»»»»»»»» C:\WINDOWS\system32 »»»»»»»»»»»»»»»»»»»»»»»» C:\WINDOWS\system32\LogFiles »»»»»»»»»»»»»»»»»»»»»»»» C:\Dokumente und Einstellungen\Patrick »»»»»»»»»»»»»»»»»»»»»»»» C:\Dokumente und Einstellungen\Patrick\Application Data »»»»»»»»»»»»»»»»»»»»»»»» Start Menu »»»»»»»»»»»»»»»»»»»»»»»» C:\DOKUME~1\Patrick\FAVORI~1 C:\DOKUME~1\Patrick\FAVORI~1\Error Cleaner.url FOUND ! C:\DOKUME~1\Patrick\FAVORI~1\Privacy Protector.url FOUND ! C:\DOKUME~1\Patrick\FAVORI~1\Spyware?Malware Protection.url FOUND ! »»»»»»»»»»»»»»»»»»»»»»»» Desktop C:\DOKUME~1\Patrick\Desktop\Error Cleaner.url FOUND ! C:\DOKUME~1\Patrick\Desktop\Privacy Protector.url FOUND ! C:\DOKUME~1\Patrick\Desktop\Spyware?Malware Protection.url FOUND ! »»»»»»»»»»»»»»»»»»»»»»»» C:\Programme »»»»»»»»»»»»»»»»»»»»»»»» Corrupted keys »»»»»»»»»»»»»»»»»»»»»»»» Desktop Components [HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Desktop\Components\0] "Source"="file:///C:\\WINDOWS\\privacy_danger\\index.htm" "SubscribedURL"="" "FriendlyName"="Privacy Protection" [HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Desktop\Components\1] "Source"="About:Home" "SubscribedURL"="About:Home" "FriendlyName"="Die derzeitige Homepage" »»»»»»»»»»»»»»»»»»»»»»»» IEDFix !!!Attention, following keys are not inevitably infected!!! IEDFix Credits: Malware Analysis & Diagnostic Code: S!Ri »»»»»»»»»»»»»»»»»»»»»»»» VACFix !!!Attention, following keys are not inevitably infected!!! »»»»»»»»»»»»»»»»»»»»»»»» 404Fix !!!Attention, following keys are not inevitably infected!!! 404Fix Credits: Malware Analysis & Diagnostic Code: S!Ri »»»»»»»»»»»»»»»»»»»»»»»» Sharedtaskscheduler !!!Attention, following keys are not inevitably infected!!! SrchSTS.exe by S!Ri Search SharedTaskScheduler's .dll »»»»»»»»»»»»»»»»»»»»»»»» AppInit_DLLs !!!Attention, following keys are not inevitably infected!!! [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows] "AppInit_DLLs"="" »»»»»»»»»»»»»»»»»»»»»»»» Winlogon !!!Attention, following keys are not inevitably infected!!! [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon] "Userinit"="C:\\WINDOWS\\system32\\userinit.exe," "System"="" »»»»»»»»»»»»»»»»»»»»»»»» Rustock »»»»»»»»»»»»»»»»»»»»»»»» DNS Description: Realtek RTL8139/810x Family Fast Ethernet NIC DNS Server Search Order: 195.34.133.21 DNS Server Search Order: 195.34.133.22 HKLM\SYSTEM\CCS\Services\Tcpip\..\{7E63C2EE-52E4-457F-A66B-03788B430BAB}: DhcpNameServer=195.34.133.21 195.34.133.22 HKLM\SYSTEM\CS1\Services\Tcpip\..\{7E63C2EE-52E4-457F-A66B-03788B430BAB}: DhcpNameServer=195.34.133.21 195.34.133.22 HKLM\SYSTEM\CS3\Services\Tcpip\..\{7E63C2EE-52E4-457F-A66B-03788B430BAB}: DhcpNameServer=195.34.133.21 195.34.133.22 HKLM\SYSTEM\CCS\Services\Tcpip\Parameters: DhcpNameServer=195.34.133.21 195.34.133.22 HKLM\SYSTEM\CS1\Services\Tcpip\Parameters: DhcpNameServer=195.34.133.21 195.34.133.22 HKLM\SYSTEM\CS3\Services\Tcpip\Parameters: DhcpNameServer=195.34.133.21 195.34.133.22 »»»»»»»»»»»»»»»»»»»»»»»» Scanning for wininet.dll infection »»»»»»»»»»»»»»»»»»»»»»»» End |
| | #2 | |
     | Bitte hilfe für: BAT/Fake.Privdanger Hi,
__________________bitte alle notwendigen Tools vorher runterladen, dann offline gehen (ev. vorher Beschreibungen etc. ausdrucken), die Beseitigung komplett durchführen und erst dann wieder online gehen (sonst besteht die Gefahr, dass Trojaner nachgeladen werden)... Bitte folgende Files prüfen: Zitat:
Oben auf der Seite --> auf Durchsuchen klicken --> Datei aussuchen (oder gleich die Datei mit korrektem Pfad einkopieren) --> Doppelklick auf die zu prüfende Datei --> klick auf "Send"... jetzt abwarten - dann mit der rechten Maustaste den Text markieren -> kopieren - einfügen Poste das Ergebnis jeweils mit Filename. Falls ein File nicht erkannt wird, unten im Avengerscript rausnehmen (bei "Files to delete")... Also: Anleitung Avenger (by swandog46) 1.) Lade dir das Tool Avenger und speichere es auf dem Desktop: 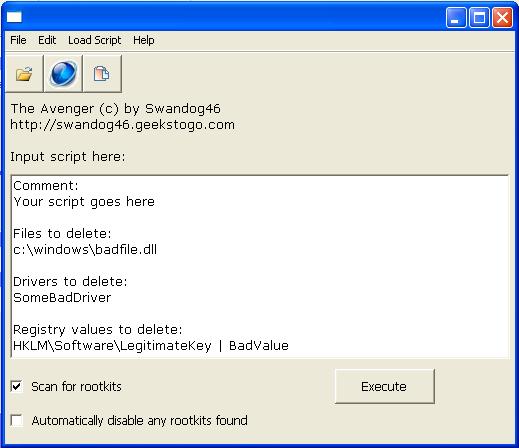 2.) Das Programm so einstellen wie es auf dem Bild zu sehen ist. Kopiere nun folgenden Text in das weiße Feld: (bei -> "input script here") Code:
ATTFilter Files to delete:
C:\WINDOWS\privacy_danger\index.htm
C:\WINDOWS\xvorfwbd.dll
C:\WINDOWS\wpvmqosg.dll
C:\WINDOWS\vrmdtneg.dll
C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL
C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL
Folders to delete:
C:\WINDOWS\privacy_danger
C:\Programme\MyWebSearch\SrchAstt\9.bin
C:\Programme\MyWebSearch\SrchAstt
C:\Programme\MyWebSearch
4.) Um den Avenger zu starten klicke auf -> Execute Dann bestätigen mit "Yes" das der Rechner neu startet! 5.) Nachdem das System neu gestartet ist, findest du hier einen Report vom Avenger -> C:\avenger.txt Öffne die Datei mit dem Editor und kopiere den gesamten Text in deinen Beitrag hier am Trojaner-Board. Hijackthis, fixen: öffne das HijackThis -- Button "scan" -- vor den nachfolgenden Einträge Häkchen setzen -- Button "Fix checked" -- PC neustarten Beim fixen müssen alle Programme geschlossen sein! Code:
ATTFilter O24 - Desktop Component 0: Privacy Protection - file:///C:\WINDOWS\privacy_danger\index.htm
O21 - SSODL: xvorfwbd - {2629C9EB-5E35-4249-A6F9-DB62B9393907} - C:\WINDOWS\xvorfwbd.dll
O21 - SSODL: wpvmqosg - {024022B6-AF69-4A6F-99E4-488B7F21DAD9} - C:\WINDOWS\wpvmqosg.dll
O9 - Extra button: ICQ Lite - {B863453A-26C3-4e1f-A54D-A2CD196348E9} - C:\Programme\ICQLite\ICQLite.exe (file missing)
O9 - Extra 'Tools' menuitem: ICQ Lite - {B863453A-26C3-4e1f-A54D-A2CD196348E9} - C:\Programme\ICQLite\ICQLite.exe (file missing)
O3 - Toolbar: vrmdtneg - {460B9C85-61E5-4CB6-A4B2-501DE81C4475} - C:\WINDOWS\vrmdtneg.dll
O2 - BHO: (no name) - {7E853D72-626A-48EC-A868-BA8D5E23E045} - (no file)
O2 - BHO: MyWebSearch Search Assistant BHO - {00A6FAF1-072E-44cf-8957-5838F569A31D} - C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.D LL
R1 - HKCU\Software\Microsoft\Internet Explorer\Main,SearchAssistant = http://search.imesh.com/sidebar.html?src=ssb
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://softwarereferral.com/jump.php?wmid=6010&mid=MjI6Ojg5&lid=2
R3 - URLSearchHook: (no name) - {00A6FAF6-072E-44cf-8957-5838F569A31D} - C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.D LL
Führe einen Systemscan durch und poste das Ergebnis! Scanne/Beseitige mit Anitmalewarebyt und Poste auch dieses Ergebnis: http://www.trojaner-board.de/51187-m...i-malware.html Poste ein neues HJ-Log; Chris
__________________ |
| | #3 |
| | Bitte hilfe für: BAT/Fake.Privdanger Hallo, vielen dank für die Antwort und nun hier die Ergebnisse.
__________________Also, ich habe die Anweisungen wie beschrieben befolgt und nun bin ich das problem los. Task-mngr und startleiste funktionieren wieder, und auch sonst is alles wie vorher. Hier der hijack log nach der ganzen aktion: Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 17:01:02, on 19.06.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180) Boot mode: Normal Running processes: C:\WINDOWS\System32\smss.exe C:\WINDOWS\system32\winlogon.exe C:\WINDOWS\system32\services.exe C:\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\svchost.exe C:\WINDOWS\System32\svchost.exe C:\WINDOWS\system32\Ati2evxx.exe C:\WINDOWS\system32\LEXBCES.EXE C:\WINDOWS\system32\LEXPPS.EXE C:\WINDOWS\system32\spoolsv.exe C:\Programme\Avira\AntiVir PersonalEdition Classic\avguard.exe C:\WINDOWS\Explorer.EXE C:\Programme\Avira\AntiVir PersonalEdition Classic\sched.exe C:\Programme\Symantec\LiveUpdate\ALUSchedulerSvc.exe C:\WINDOWS\System32\svchost.exe C:\Programme\Gemeinsame Dateien\Microsoft Shared\VS7DEBUG\MDM.EXE C:\Programme\Alcohol Soft\Alcohol 120\StarWind\StarWindServiceAE.exe C:\WINDOWS\system32\wuauclt.exe C:\Programme\Trend Micro\HijackThis\HijackThis.exe C:\WINDOWS\system32\wuauclt.exe O23 - Service: AntiVir PersonalEdition Classic Planer (AntiVirScheduler) - Avira GmbH - C:\Programme\Avira\AntiVir PersonalEdition Classic\sched.exe O23 - Service: AntiVir PersonalEdition Classic Guard (AntiVirService) - Avira GmbH - C:\Programme\Avira\AntiVir PersonalEdition Classic\avguard.exe O23 - Service: Ati HotKey Poller - ATI Technologies Inc. - C:\WINDOWS\system32\Ati2evxx.exe O23 - Service: Automatisches LiveUpdate - Scheduler - Symantec Corporation - C:\Programme\Symantec\LiveUpdate\ALUSchedulerSvc.exe O23 - Service: Symantec Lic NetConnect service (CLTNetCnService) - Unknown owner - C:\Programme\Gemeinsame Dateien\Symantec Shared\ccSvcHst.exe (file missing) O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Programme\Gemeinsame Dateien\InstallShield\Driver\1050\Intel 32\IDriverT.exe O23 - Service: LexBce Server (LexBceS) - Lexmark International, Inc. - C:\WINDOWS\system32\LEXBCES.EXE O23 - Service: LiveUpdate Notice Service Ex (LiveUpdate Notice Ex) - Unknown owner - C:\Programme\Gemeinsame Dateien\Symantec Shared\ccSvcHst.exe (file missing) O23 - Service: PC Tools Auxiliary Service (sdAuxService) - PC Tools - C:\Programme\Spyware Doctor\pctsAuxs.exe O23 - Service: PC Tools Security Service (sdCoreService) - PC Tools - C:\Programme\Spyware Doctor\pctsSvc.exe O23 - Service: StarWind AE Service (StarWindServiceAE) - Rocket Division Software - C:\Programme\Alcohol Soft\Alcohol 120\StarWind\StarWindServiceAE.exe -- End of file - 2594 bytes Hier der Avenger Log: Logfile of The Avenger Version 2.0, (c) by Swandog46 Swandog46's Public Anti-Malware Tools Platform: Windows XP ******************* Script file opened successfully. Script file read successfully. Backups directory opened successfully at C:\Avenger ******************* Beginning to process script file: Rootkit scan active. No rootkits found! Error: could not open file "C:\WINDOWS\privacy_danger\index.htm" Deletion of file "C:\WINDOWS\privacy_danger\index.htm" failed! Status: 0xc000003a (STATUS_OBJECT_PATH_NOT_FOUND) --> bad path / the parent directory does not exist File "C:\WINDOWS\xvorfwbd.dll" deleted successfully. File "C:\WINDOWS\wpvmqosg.dll" deleted successfully. File "C:\WINDOWS\vrmdtneg.dll" deleted successfully. File "C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL" deleted successfully. Error: file "C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL" not found! Deletion of file "C:\Programme\MyWebSearch\SrchAstt\9.bin\MWSSRCAS.DLL" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Error: folder "C:\WINDOWS\privacy_danger" not found! Deletion of folder "C:\WINDOWS\privacy_danger" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Folder "C:\Programme\MyWebSearch\SrchAstt\9.bin" deleted successfully. Folder "C:\Programme\MyWebSearch\SrchAstt" deleted successfully. Folder "C:\Programme\MyWebSearch" deleted successfully. Completed script processing. ******************* Finished! Terminate. Und zu guter letzt der Malwarebytes Log: Malwarebytes' Anti-Malware 1.17 Datenbank Version: 869 16:57:47 19.06.2008 mbam-log-6-19-2008 (16-57-47).txt Scan Art: Komplett Scan (C:\|D:\|) Objekte gescannt: 237676 Scan Dauer: 58 minute(s), 27 second(s) Infizierte Speicher Prozesse: 0 Infizierte Speicher Module: 0 Infizierte Registrierungsschlüssel: 42 Infizierte Registrierungswerte: 1 Infizierte Datei Objekte der Registrierung: 15 Infizierte Verzeichnisse: 0 Infizierte Dateien: 21 Infizierte Speicher Prozesse: (Keine Malware Objekte gefunden) Infizierte Speicher Module: (Keine Malware Objekte gefunden) Infizierte Registrierungsschlüssel: HKEY_CLASSES_ROOT\CLSID\{00a6faf6-072e-44cf-8957-5838f569a31d} (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\CLSID\{147a976f-eee1-4377-8ea7-4716e4cdd239} (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\CLSID\{9afb8248-617f-460d-9366-d71cdeda3179} (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{56256a51-b582-467e-b8d4-7786eda79ae0} (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Trymedia Systems (Adware.Trymedia) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\vrmdtneg.bkrn (Trojan.FakeAlert) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\vrmdtneg.toolbar.1 (Trojan.FakeAlert) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.htmlpanel (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.htmlpanel.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.outlookaddin (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.outlookaddin.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.pseudotransparentplugin (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearch.pseudotransparentplugin.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearchtoolbar.settingsplugin (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearchtoolbar.settingsplugin.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearchtoolbar.toolbarplugin (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\mywebsearchtoolbar.toolbarplugin.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.datacontrol (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.datacontrol.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.historykillerscheduler (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.historykillerscheduler.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.historyswattercontrolbar (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.historyswattercontrolbar.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.htmlmenu (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.htmlmenu.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.htmlmenu.2 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.iecookiesmanager (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.iecookiesmanager.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.killerobjmanager (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.killerobjmanager.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.popswatterbarbutton (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.popswatterbarbutton.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.popswattersettingscontrol (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.popswattersettingscontrol.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.shellviewcontrol (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\funwebproducts.shellviewcontrol.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\screensavercontrol.screensaverinstaller (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_CLASSES_ROOT\screensavercontrol.screensaverinstaller.1 (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_LOCAL_MACHINE\SOFTWARE\MyWebSearch (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Multimedia\WMPlayer\Schemes\f3pss (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_LOCAL_MACHINE\SOFTWARE\Fun Web Products (Adware.MyWebSearch) -> Quarantined and deleted successfully. HKEY_LOCAL_MACHINE\SOFTWARE\FocusInteractive (Adware.MyWebSearch) -> Quarantined and deleted successfully. Infizierte Registrierungswerte: HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\{b7d3e479-cc68-42b5-a338-938ece35f419} (Adware.Softomate) -> Quarantined and deleted successfully. Infizierte Datei Objekte der Registrierung: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductId (Trojan.FakeAlert) -> Bad: (VIRUS ALERT!) Good: (76416-OEM-0011903-00117) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Control Panel\International\sTimeFormat (Trojan.FakeAlert) -> Bad: (HH:mm: VIRUS ALERT!) Good: (HH:mm:ss) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowControlPanel (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowRun (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowSearch (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowHelp (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowMyDocs (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_ShowMyComputer (Hijack.StartMenu) -> Bad: (0) Good: (1) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoStartMenuMorePrograms (Hijack.StartMenu) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\StartMenuLogOff (Hijack.StartMenu) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoDrives (Hijack.Drives) -> Bad: (12) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoToolbarCustomize (Hijack.Explorer) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoSetFolders (Hijack.Explorer) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableTaskMgr (Hijack.TaskManager) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System\NoDispCPL (Hijack.DisplayProperties) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully. Infizierte Verzeichnisse: (Keine Malware Objekte gefunden) Infizierte Dateien: C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108230.EXE (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108232.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108234.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108236.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108238.SCR (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108240.DLL (Adware.MyWeb.FunWeb) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108241.EXE (Adware.MyWeb.FunWeb) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108242.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108244.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108247.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108248.DLL (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108251.EXE (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108253.EXE (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\System Volume Information\_restore{B7DA89BD-ED33-477E-8EA2-34F25F2FDCEC}\RP584\A0108259.dll (Trojan.FalkeAlert) -> Quarantined and deleted successfully. C:\WINDOWS\system32\f3PSSavr.scr (Adware.MyWebSearch) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Desktop\Spyware&Malware Protection.url (Rogue.Link) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Desktop\Privacy Protector.url (Rogue.Link) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Desktop\Error Cleaner.url (Rogue.Link) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Favoriten\Error Cleaner.url (Rogue.Link) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Favoriten\Privacy Protector.url (Rogue.Link) -> Quarantined and deleted successfully. C:\Dokumente und Einstellungen\Patrick\Favoriten\Spyware&Malware Protection.url (Rogue.Link) -> Quarantined and deleted successfully. Vielen, vielen dank für die schnelle Hilfe, alleine hätt ich das nicht geschafft. Syrak |
 |
| Themen zu Bitte hilfe für: BAT/Fake.Privdanger |
| abgesicherten modus, analysis, antivir, application, attention, avira, bho, desktop, error, excel, firefox, helper, hijack, hijackthis, hkus\s-1-5-18, home, homepage, keine ahnung, malware, mozilla firefox, privacy protection, problem, realtek, security, server, software, spyware, symantec, system, urlsearchhook, userinit.exe, windows, windows xp, wmid |