
 |
| |||||||
Plagegeister aller Art und deren Bekämpfung: setup.exe blockiertWindows 7 Wenn Du nicht sicher bist, ob Du dir Malware oder Trojaner eingefangen hast, erstelle hier ein Thema. Ein Experte wird sich mit weiteren Anweisungen melden und Dir helfen die Malware zu entfernen oder Unerwünschte Software zu deinstallieren bzw. zu löschen. Bitte schildere dein Problem so genau wie möglich. Sollte es ein Trojaner oder Viren Problem sein wird ein Experte Dir bei der Beseitigug der Infektion helfen. |
 |
| |
| | #1 |
 | setup.exe blockiert hallo zusammen, hab mal mein erstes GROSSES Problem ich hab mir mal eine datei heruntergeladen (über limewire), hab dann auf die vorhandene Setup.exe geklickt, dann stand da "Fehler...." und seitdem wurden meine automatischen updates für mein "Windows XP home editon" abgeschaltet und wenn ich sie wieder anschalten wollte tat sich nichts. auch kann ich keine virendurchsuchung mehr mit meinem Trend micro PC-cillin internet security 2007 durchführen. jede stunde oder so zeigt mir die Internet security an dass ich eine verbindung auf eine gefährliche internetseite herstellen will, obwohl ich keinen einzigen browser gestartet habe, das ist dann irgend so eine seite mit einer ip-adresse am anfang. Ich wollte mir dann einen freeware scanner runterladen, doch den konnte ich erst gar nicht installieren. wo ich dann am nächsten tag meinen pc startete fand meine internet seceurity einen Virus, hat ihn dann auch gleich gelöscht. doch geändert hat sich dadurch nichts. Darauf fand sie noch einen Virus in C:\System Volume Information\ konnte ihn aber nicht löschen sie wies mich darauf an ihn manuel zu löschen doch ich habe auf diesen Ordner keinen zugriff sagt mir das system. es ist zum kotzen, mein PC ist dermaßen lahm ich hoffe ihr könnt mir helfen lg matthias Logfile of Trend Micro HijackThis v2.0.2 Scan saved at 08:18:31, on 03.06.2008 Platform: Windows XP SP2 (WinNT 5.01.2600) MSIE: Internet Explorer v7.00 (7.00.6000.16640) Boot mode: Normal Running processes: C:\WINDOWS\System32\smss.exe C:\WINDOWS\system32\winlogon.exe C:\WINDOWS\system32\services.exe C:\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\svchost.exe C:\WINDOWS\System32\svchost.exe C:\WINDOWS\system32\spoolsv.exe C:\WINDOWS\system32\cisvc.exe C:\WINDOWS\system32\E_S00RP1.EXE C:\PROGRA~1\TRENDM~1\INTERN~1\PcCtlCom.exe C:\WINDOWS\system32\SAgent4.exe C:\WINDOWS\system32\svchost.exe C:\PROGRA~1\TRENDM~1\INTERN~1\Tmntsrv.exe C:\PROGRA~1\TRENDM~1\INTERN~1\TmPfw.exe C:\WINDOWS\SOUNDMAN.EXE C:\WINDOWS\system32\igfxtray.exe C:\Programme\KGB\Mpk.exe C:\Programme\Trend Micro\Internet Security 2007\pccguide.exe C:\WINDOWS\system32\rundll32.exe C:\Programme\Java\jre1.6.0_05\bin\jusched.exe C:\Programme\QuickTime\qttask.exe C:\WINDOWS\system32\rundll32.exe C:\Programme\Unlocker\UnlockerAssistant.exe C:\Programme\Trend Micro\Internet Security 2007\TMAS_OE\TMAS_OEMon.exe C:\WINDOWS\system32\Rundll32.exe C:\Programme\DSL-Manager\DslMgr.exe C:\WINDOWS\system32\wscntfy.exe C:\Programme\DSL-Manager\DslMgrSvc.exe C:\PROGRA~1\TRENDM~1\INTERN~1\PcScnSrv.exe C:\WINDOWS\system32\cidaemon.exe C:\WINDOWS\explorer.exe C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Communicator\xcommsvr.exe C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Scan Server\bdss.exe C:\Programme\Softwin\BitDefender10\vsserv.exe C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Update Service\livesrv.exe C:\Programme\Softwin\BitDefender10\bdagent.exe C:\Programme\Softwin\BitDefender10\bdmcon.exe C:\WINDOWS\system32\rundll32.exe C:\Programme\Mozilla Firefox\firefox.exe C:\PROGRA~1\TRENDM~1\INTERN~1\tmproxy.exe C:\Dokumente und Einstellungen\Fuß\Desktop\HiJackThis.exe R1 - HKCU\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896 R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = about:blank R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896 R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896 R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157 R0 - HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant = R0 - HKLM\Software\Microsoft\Internet Explorer\Search,CustomizeSearch = R1 - HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings,ProxyServer = 192.168.2.1:80 O3 - Toolbar: EPSON Web-To-Page - {EE5D279F-081B-4404-994D-C6B60AAEBA6D} - C:\Programme\EPSON\EPSON Web-To-Page\EPSON Web-To-Page.dll O3 - Toolbar: &Google - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - c:\programme\google\googletoolbar1.dll O3 - Toolbar: (no name) - {7b3b29e7-3696-45d4-b59c-48f2803b3e36} - (no file) O3 - Toolbar: ImageShack Toolbar - {6932D140-ABC4-4073-A44C-D4A541665E35} - C:\Programme\ImageShackToolbar\ImageShackToolbar.dll O3 - Toolbar: Kwyshell MidpX - {EBE9E2B5-B526-48BC-AD46-687263EDCB0E} - C:\Programme\Kwyshell\MidpX\JadInvoker\MidpInvoker.dll O4 - HKLM\..\Run: [SoundMan] SOUNDMAN.EXE O4 - HKLM\..\Run: [IgfxTray] C:\WINDOWS\system32\igfxtray.exe O4 - HKLM\..\Run: [EPSON Stylus CX3600 Series] C:\WINDOWS\System32\spool\DRIVERS\W32X86\3\E_FATI9BE.EXE /P26 "EPSON Stylus CX3600 Series" /O6 "USB001" /M "Stylus CX3600" O4 - HKLM\..\Run: [_winadm] C:\WINDOWS\system32\winadm.exe O4 - HKLM\..\Run: [pccguide.exe] "C:\Programme\Trend Micro\Internet Security 2007\pccguide.exe" O4 - HKLM\..\Run: [BluetoothAuthenticationAgent] rundll32.exe bthprops.cpl,,BluetoothAuthenticationAgent O4 - HKLM\..\Run: [SunJavaUpdateSched] "C:\Programme\Java\jre1.6.0_05\bin\jusched.exe" O4 - HKLM\..\Run: [QuickTime Task] "C:\Programme\QuickTime\qttask.exe" -atboottime O4 - HKLM\..\Run: [Adobe Reader Speed Launcher] "C:\Programme\Adobe\Reader 8.0\Reader\Reader_sl.exe" O4 - HKLM\..\Run: [UnlockerAssistant] "C:\Programme\Unlocker\UnlockerAssistant.exe" O4 - HKLM\..\Run: [94d0754d] rundll32.exe "C:\WINDOWS\system32\rsrvabru.dll",b O4 - HKLM\..\Run: [BM97e346d1] Rundll32.exe "C:\WINDOWS\system32\csjgitae.dll",s O4 - HKLM\..\Run: [Antivirus] C:\Programme\VAV\vav.exe O4 - HKLM\..\Run: [BDMCon] "C:\Programme\Softwin\BitDefender10\bdmcon.exe" /reg O4 - HKLM\..\Run: [BDAgent] "C:\Programme\Softwin\BitDefender10\bdagent.exe" O4 - HKCU\..\Run: [NBJ] "C:\Programme\Ahead\Nero BackItUp\NBJ.exe" O4 - HKCU\..\Run: [EPSON Stylus CX3600 Series] C:\WINDOWS\System32\spool\DRIVERS\W32X86\3\E_FATI9BE.EXE /P26 "EPSON Stylus CX3600 Series" /M "Stylus CX3600" /EF "HKCU" O4 - HKCU\..\Run: [OE] "C:\Programme\Trend Micro\Internet Security 2007\TMAS_OE\TMAS_OEMon.exe" O4 - HKCU\..\Run: [Windows Update] C:\WINDOWS\system32\scvhost.exe O4 - HKCU\..\Run: [Antivirus] C:\Programme\VAV\vav.exe O4 - HKLM\..\Policies\Explorer\Run: [Mpk.exe] C:\Programme\KGB\Mpk.exe O4 - HKUS\S-1-5-21-839522115-1682526488-2147125571-1009\..\Run: [swg] C:\Programme\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe (User 'Matthias') O4 - HKUS\S-1-5-21-839522115-1682526488-2147125571-1009\..\Run: [NBJ] "C:\Programme\Ahead\Nero BackItUp\NBJ.exe" (User 'Matthias') O4 - HKUS\S-1-5-21-839522115-1682526488-2147125571-1009\..\Run: [Steam] "c:\programme\steam\steam.exe" -silent (User 'Matthias') O4 - S-1-5-18 Startup: DSL-Manager.lnk = C:\Programme\DSL-Manager\DslMgr.exe (User 'SYSTEM') O4 - .DEFAULT Startup: DSL-Manager.lnk = C:\Programme\DSL-Manager\DslMgr.exe (User 'Default user') O4 - Startup: DSL-Manager.lnk = C:\Programme\DSL-Manager\DslMgr.exe O4 - Global Startup: Microsoft Office.lnk = C:\Programme\Microsoft Office\Office10\OSA.EXE O4 - Global Startup: VR-NetWorld Auftragsprüfung.lnk = C:\Programme\VR-NetWorld\VRToolCheckOrder.exe O6 - HKCU\Software\Policies\Microsoft\Internet Explorer\Restrictions present O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Control Panel present O9 - Extra button: (no name) - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Programme\Java\jre1.6.0_05\bin\npjpi160_05.dll O9 - Extra 'Tools' menuitem: Sun Java Konsole - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Programme\Java\jre1.6.0_05\bin\npjpi160_05.dll O9 - Extra button: ShopperReports - Compare product prices - {C5428486-50A0-4a02-9D20-520B59A9F9B2} - C:\Programme\ShoppingReport\Bin\2.0.21\ShoppingReport.dll O9 - Extra button: ShopperReports - Compare travel rates - {C5428486-50A0-4a02-9D20-520B59A9F9B3} - C:\Programme\ShoppingReport\Bin\2.0.21\ShoppingReport.dll O9 - Extra button: (no name) - {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - (no file) O9 - Extra button: (no name) - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe O9 - Extra 'Tools' menuitem: @xpsp3res.dll,-20001 - {e2e2dd38-d088-4134-82b7-f2ba38496583} - C:\WINDOWS\Network Diagnostic\xpnetdiag.exe O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Programme\Messenger\msmsgs.exe O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Programme\Messenger\msmsgs.exe O16 - DPF: {6932D140-ABC4-4073-A44C-D4A541665E35} (ImageShack Toolbar) - http://toolbar.imageshack.us/toolbar/ImageShackToolbar.cab O16 - DPF: {B8BE5E93-A60C-4D26-A2DC-220313175592} (ZoneIntro Class) - http://cdn2.zone.msn.com/binFramework/v10/ZIntro.cab34246.cab O16 - DPF: {FD0B6769-6490-4A91-AA0A-B5AE0DC75AC9} (Performance Viewer Activex Control) - https://secure.logmein.com/activex/RACtrl.cab O18 - Filter hijack: text/html - {2AB289AE-4B90-4281-B2AE-1F4BB034B647} - (no file) O23 - Service: BitDefender Scan Server (bdss) - Unknown owner - C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Scan Server\bdss.exe O23 - Service: EPSON V3 Service2(03) (EPSON_PM_RPCV2_01) - SEIKO EPSON CORPORATION - C:\WINDOWS\system32\E_S00RP1.EXE O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Programme\Gemeinsame Dateien\InstallShield\Driver\1150\Intel 32\IDriverT.exe O23 - Service: BitDefender Desktop Update Service (LIVESRV) - SOFTWIN S.R.L. - C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Update Service\livesrv.exe O23 - Service: Trend Micro Central Control Component (PcCtlCom) - Trend Micro Inc. - C:\PROGRA~1\TRENDM~1\INTERN~1\PcCtlCom.exe O23 - Service: Trend Micro Spyware-Schutz (PcScnSrv) - Trend Micro Inc. - C:\PROGRA~1\TRENDM~1\INTERN~1\PcScnSrv.exe O23 - Service: Epson Printer Status Agent4 (StatusAgent4) - SEIKO EPSON CORPORATION - C:\WINDOWS\system32\SAgent4.exe O23 - Service: DSL-Manager (TDslMgrService) - T-Systems Enterprise Services GmbH - C:\Programme\DSL-Manager\DslMgrSvc.exe O23 - Service: Trend Micro Real-time Service (Tmntsrv) - Trend Micro Inc. - C:\PROGRA~1\TRENDM~1\INTERN~1\Tmntsrv.exe O23 - Service: Trend Micro Personal Firewall (TmPfw) - Trend Micro Inc. - C:\PROGRA~1\TRENDM~1\INTERN~1\TmPfw.exe O23 - Service: Trend Micro Proxy Service (tmproxy) - Trend Micro Inc. - C:\PROGRA~1\TRENDM~1\INTERN~1\tmproxy.exe O23 - Service: Tor Win32 Service (tor) - Unknown owner - C:\Programme\Vidalia Bundle\Tor\tor.exe O23 - Service: BitDefender Virus Shield (VSSERV) - SOFTWIN S.R.L. - C:\Programme\Softwin\BitDefender10\vsserv.exe O23 - Service: BitDefender Communicator (XCOMM) - SOFTWIN S.R.L - C:\Programme\Gemeinsame Dateien\Softwin\BitDefender Communicator\xcommsvr.exe O24 - Desktop Component 0: (no name) - -- End of file - 9864 bytes |
| | #2 | |
     | setup.exe blockiert Hi,
__________________voll erwischt; Wenn schon zweifelhafte Quellen, dann vorher online prüfen lassen! Bitte folgende Files prüfen: Zitat:
Oben auf der Seite --> auf Durchsuchen klicken --> Datei aussuchen (oder gleich die Datei mit korrektem Pfad einkopieren) --> Doppelklick auf die zu prüfende Datei --> klick auf "Send"... jetzt abwarten - dann mit der rechten Maustaste den Text markieren -> kopieren - einfügen Poste die Ergebnisse mit Filename, nicht erkannte Files unten rausnehmen (Avenger/HJ)! Also: Anleitung Avenger (by swandog46) 1.) Lade dir das Tool Avenger und speichere es auf dem Desktop: 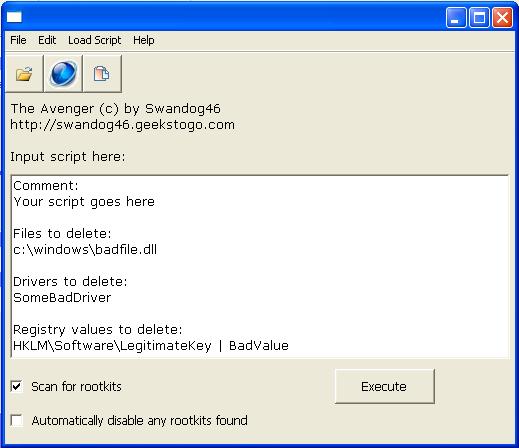 2.) Das Programm so einstellen wie es auf dem Bild zu sehen ist. Kopiere nun folgenden Text in das weiße Feld: (bei -> "input script here") Code:
ATTFilter Registry values to delete:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Mpk.exe
HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Windows Update
HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus
HKLM\Software\Microsoft\Windows\CurrentVersion\Run|94d0754d
HKCU\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus
Files to delete:
C:\WINDOWS\system32\scvhost.exe
C:\Programme\VAV\vav.exe
C:\WINDOWS\system32\rsrvabru.dll
C:\WINDOWS\system32\csjgitae.dll
C:\Programme\KGB\Mpk.exe
4.) Um den Avenger zu starten klicke auf -> Execute Dann bestätigen mit "Yes" das der Rechner neu startet! 5.) Nachdem das System neu gestartet ist, findest du hier einen Report vom Avenger -> C:\avenger.txt Öffne die Datei mit dem Editor und kopiere den gesamten Text in deinen Beitrag hier am Trojaner-Board. Hijackthis, fixen: öffne das HijackThis -- Button "scan" -- vor den nachfolgenden Einträge Häkchen setzen -- Button "Fix checked" -- PC neustarten Beim fixen müssen alle Programme geschlossen sein! Code:
ATTFilter O24 - Desktop Component 0: (no name) -
O18 - Filter hijack: text/html - {2AB289AE-4B90-4281-B2AE-1F4BB034B647} - (no file)
O9 - Extra button: (no name) - {CD67F990-D8E9-11d2-98FE-00C0F0318AFE} - (no file)
O9 - Extra button: ShopperReports - Compare product prices - {C5428486-50A0-4a02-9D20-520B59A9F9B2} - C:\Programme\ShoppingReport\Bin\2.0.21\ShoppingRep ort.dll
O9 - Extra button: ShopperReports - Compare travel rates - {C5428486-50A0-4a02-9D20-520B59A9F9B3} - C:\Programme\ShoppingReport\Bin\2.0.21\ShoppingRep ort.dll
O4 - HKCU\..\Run: [Windows Update] C:\WINDOWS\system32\scvhost.exe
O4 - HKCU\..\Run: [Antivirus] C:\Programme\VAV\vav.exe
O4 - HKLM\..\Policies\Explorer\Run: [Mpk.exe] C:\Programme\KGB\Mpk.exe
O4 - HKLM\..\Run: [94d0754d] rundll32.exe "C:\WINDOWS\system32\rsrvabru.dll",b
O4 - HKLM\..\Run: [BM97e346d1] Rundll32.exe "C:\WINDOWS\system32\csjgitae.dll",s
O4 - HKLM\..\Run: [Antivirus] C:\Programme\VAV\vav.exe
O3 - Toolbar: (no name) - {7b3b29e7-3696-45d4-b59c-48f2803b3e36} - (no file)
Art
Lade ComboFix von http://download.bleepingcomputer.com/sUBs/ComboFix.exe und speichert es auf den Desktop. Alle Fenster schliessen und combofix.exe starten und bestätige die folgende Abfrage mit 1 und drücke Enter. Der Scan mit Combofix kann einige Zeit in Anspruch nehmen, also habe etwas Geduld. Während des Scans bitte nichts am Rechner unternehmen Es kann möglich sein, dass der Rechner zwischendurch neu gestartet wird. Nach Scanende wird ein Report angezeigt, den bitte kopieren und in deinem Thread einfuegen. Weitere Anleitung unter:Ein Leitfaden und Tutorium zur Nutzung von ComboFix Antimalewarebyte: http://www.trojaner-board.de/51187-a...i-malware.html Poste alle Logs und ein neues HJ-Log... Chris
__________________ |
| | #3 | |
 | setup.exe blockiertZitat:
ich hab jetzt die Files gescannt jetzt werde ich gleich "The Avenger" starten rsrvabrv.dll: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.5.30.1 2008.06.03 - AntiVir 7.8.0.26 2008.06.03 - Authentium 5.1.0.4 2008.06.02 - Avast 4.8.1195.0 2008.06.03 - AVG 7.5.0.516 2008.06.03 - BitDefender 7.2 2008.06.03 - CAT-QuickHeal 9.50 2008.06.02 - ClamAV 0.92.1 2008.06.02 - DrWeb 4.44.0.09170 2008.06.03 - eSafe 7.0.15.0 2008.06.02 - eTrust-Vet 31.4.5844 2008.06.03 - Ewido 4.0 2008.06.02 - F-Prot 4.4.4.56 2008.06.02 - F-Secure 6.70.13260.0 2008.06.03 - Fortinet 3.14.0.0 2008.06.03 - GData 2.0.7306.1023 2008.06.03 - Ikarus T3.1.1.26.0 2008.06.03 - Kaspersky 7.0.0.125 2008.06.03 - McAfee 5308 2008.06.02 - Microsoft 1.3604 2008.06.03 - NOD32v2 3153 2008.06.03 Win32/Adware.Virtumonde Norman 5.80.02 2008.06.02 - Panda 9.0.0.4 2008.06.02 - Prevx1 V2 2008.06.03 Fraudulent Security Program Rising 20.47.11.00 2008.06.03 - Sophos 4.29.0 2008.06.03 - Sunbelt 3.0.1143.1 2008.06.03 - Symantec 10 2008.06.03 - TheHacker 6.2.92.332 2008.06.03 - VBA32 3.12.6.7 2008.06.03 - VirusBuster 4.3.26:9 2008.06.02 - Webwasher-Gateway 6.6.2 2008.06.03 Win32.Malware.gen!90 (suspicious) weitere Informationen File size: 95232 bytes MD5...: fea4331b2193221270f890a93e5aec96 SHA1..: ec78827fe262f9320773bead777e541ffe0a8b37 SHA256: 2b2250c00f92621940daffad99121567affdaed348ce90813634955faf77cb22 SHA512: 5173058a01ee1816aa973a6cde2844fbcf4beb71f999687c4cc3def1378098f3 1c70795358612cfe85eee862b2bbe6c57addc259bbd12d3a3c8436a01f12e56f PEiD..: - PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x100016b8 timedatestamp.....: 0x42c19298 (Tue Jun 28 18:10:32 2005) machinetype.......: 0x14c (I386) ( 5 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x5000 0x4800 2.54 966495f8964a4d9a43e8022b451c1760 .data 0x6000 0x2c000 0x10400 7.95 cdf0bc94993b83695409c80090437d10 .rdata 0x32000 0x1000 0xc00 6.02 3dc6f3e278f2106c5f96f880bff1182f .rsrc 0x33000 0x1000 0xc00 4.40 7619709af006852fab73382cf8108a4b .reloc 0x34000 0x1000 0xc00 1.40 5a5b1542c6f7be1f6b5baa386783c48a ( 4 imports ) > GDI32.DLL: CreateBitmapIndirect, GetWindowOrgEx, DescribePixelFormat, GdiSetPixelFormat, GetObjectA, GdiConvertAndCheckDC, GetTextFaceW, GdiCreateLocalEnhMetaFile, GetStretchBltMode, GetRgnBox, SetPolyFillMode, ExtEscape, GdiPlayJournal, GdiEntry1, SelectBrushLocal, ChoosePixelFormat, IntersectClipRect, AddFontResourceA, EnumICMProfilesA, GdiReleaseLocalDC, RealizePalette, GetMetaRgn, SetICMProfileW, GetViewportOrgEx, CopyMetaFileA, CopyMetaFileW, PolylineTo, GdiGetBatchLimit, GdiGetCharDimensions, OffsetClipRgn, BitBlt, CopyEnhMetaFileA, SetTextJustification, GdiConvertMetaFilePict, EqualRgn > KERNEL32.DLL: FlushInstructionCache, OpenSemaphoreW, DisconnectNamedPipe, GetConsoleAliasesLengthA, VirtualAlloc, OutputDebugStringW, GetConsoleTitleW, SetProcessWorkingSetSize, GetNamedPipeHandleStateW, WriteConsoleOutputW, ExitProcess, _hread, SetThreadAffinityMask, QueueUserAPC > OLE32.DLL: CoGetObject, OleCreateMenuDescriptor, CreateOleAdviseHolder, HBITMAP_UserMarshal, CreateFileMoniker, WdtpInterfacePointer_UserUnmarshal, OleConvertIStorageToOLESTREAM, CreateILockBytesOnHGlobal, CoTaskMemAlloc, WriteFmtUserTypeStg, CoRegisterMallocSpy, MonikerCommonPrefixWith, IsValidInterface, DoDragDrop, CoGetInterfaceAndReleaseStream, STGMEDIUM_UserUnmarshal, EnableHookObject, CoQueryClientBlanket, CoMarshalInterface, WriteStringStream, CLIPFORMAT_UserUnmarshal, OleCreateStaticFromData, HGLOBAL_UserUnmarshal, UtGetDvtd32Info, WriteClassStg, HPALETTE_UserUnmarshal, OleDuplicateData, OleCreateLink > OLEAUT32.DLL: VARIANT_UserFree, VarUI2FromR4, VarUI2FromR8, VarBoolFromI2, VarR8FromUI4, VarI1FromBool, VarI1FromCy, VarCyFromR4, SafeArrayDestroyData, RevokeActiveObject, VarUI2FromStr, VarDateFromI1, VarI4FromI2, DllGetClassObject, SafeArrayAccessData, VarR8FromDisp, VarR4FromI1, GetErrorInfo, VarDecFromUI1, VarI2FromBool, VarI2FromStr, SafeArrayPutElement, DispGetParam ( 0 exports ) csjgitae.dll: Antivirus Version letzte aktualisierung Ergebnis AhnLab-V3 2008.5.30.1 2008.06.03 - AntiVir 7.8.0.26 2008.06.03 - Authentium 5.1.0.4 2008.06.02 - Avast 4.8.1195.0 2008.06.03 - AVG 7.5.0.516 2008.06.03 - BitDefender 7.2 2008.06.03 - CAT-QuickHeal 9.50 2008.06.02 - ClamAV 0.92.1 2008.06.02 - DrWeb 4.44.0.09170 2008.06.03 - eSafe 7.0.15.0 2008.06.02 - eTrust-Vet 31.4.5844 2008.06.03 - Ewido 4.0 2008.06.02 - F-Prot 4.4.4.56 2008.06.02 - F-Secure 6.70.13260.0 2008.06.03 - Fortinet 3.14.0.0 2008.06.03 - GData 2.0.7306.1023 2008.06.03 - Ikarus T3.1.1.26.0 2008.06.03 - Kaspersky 7.0.0.125 2008.06.03 - McAfee 5308 2008.06.02 - Microsoft 1.3604 2008.06.03 - NOD32v2 3153 2008.06.03 - Norman 5.80.02 2008.06.02 W32/Virtumonde.WOU Panda 9.0.0.4 2008.06.02 - Prevx1 V2 2008.06.03 Fraudulent Security Program Rising 20.47.11.00 2008.06.03 - Sophos 4.29.0 2008.06.03 - Sunbelt 3.0.1143.1 2008.06.03 - Symantec 10 2008.06.03 - TheHacker 6.2.92.332 2008.06.03 - VBA32 3.12.6.7 2008.06.03 - VirusBuster 4.3.26:9 2008.06.02 - Webwasher-Gateway 6.6.2 2008.06.03 Win32.Malware.gen!90 (suspicious) weitere Informationen File size: 104448 bytes MD5...: 0cd9dc5d7482cac5195857e51c0a7f80 SHA1..: e560ea6317a5ef16ac53473d2ab53a0745b25c2b SHA256: 5d5e98519534ffbabbaf56c971546feb32394587d4b3afd59576499284a2def9 SHA512: 263938443be2ffd7f7f058356fc07a66249f6f2f94c70ba4a432a04dfa6f7fc9 50f266a4f94ec467a60911f049ff822fa2f95356d363c45334c6c680b2f155ad PEiD..: - PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x10001718 timedatestamp.....: 0x413604db (Wed Sep 01 17:20:27 2004) machinetype.......: 0x14c (I386) ( 5 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x5000 0x4c00 2.01 91f3f42940885c8110c355e875127bee .data 0x6000 0x35000 0x12800 7.96 0a38529b91da0dbd65c8b4bcae6f0b27 .rdata 0x3b000 0x1000 0xc00 4.97 e9bb5f0c867fe874894510cae0fc9753 .rsrc 0x3c000 0x1000 0x1000 4.51 edc0bc96c76b21a08f57e4522c7db024 .reloc 0x3d000 0x1000 0x400 2.62 767a97efc487a97cb1c3385400717dc4 ( 3 imports ) > GDI32.DLL: GetObjectType, GetMetaRgn, GdiComment, GetTextCharset, GdiGetBatchLimit, bInitSystemAndFontsDirectoriesW, PolyPatBlt, PlayEnhMetaFileRecord, ExtTextOutA, GetPath, CreateScalableFontResourceW, SetViewportOrgEx, GetNearestColor, RectInRegion, CreateColorSpaceA, GdiEntry2, CloseFigure, AddFontResourceTracking, GetStockObject, CreateFontW, CreateEnhMetaFileA, GetCharWidthA, SetICMProfileA, GdiGetCharDimensions > KERNEL32.DLL: VirtualLock, SetConsoleTextAttribute, SetConsoleCtrlHandler, ReadFileEx, GetModuleFileNameW, BackupWrite, GetNumberFormatA, GetDateFormatW, SetConsoleDisplayMode, LocalCompact, TryEnterCriticalSection, IsDebuggerPresent, OutputDebugStringA, GetDriveTypeW, RtlFillMemory, SetConsoleNumberOfCommandsW, FatalExit, DebugBreak, WriteConsoleW, EnumTimeFormatsA, PeekNamedPipe, VirtualAlloc, VirtualFreeEx, SetConsoleMenuClose, GetDiskFreeSpaceExW, GlobalReAlloc, AddConsoleAliasA, GetPrivateProfileStringW, OpenProfileUserMapping, SetSystemTime, ExitProcess, WriteFileEx, EnumCalendarInfoA, GlobalAddAtomW, SetLocaleInfoW, QueryPerformanceCounter, EnumResourceTypesA > OLE32.DLL: CoQueryAuthenticationServices, CreateAntiMoniker, CoRegisterPSClsid, SNB_UserFree, CreateILockBytesOnHGlobal, StringFromCLSID, CoLockObjectExternal, HACCEL_UserFree, StgSetTimes, OleCreateFromDataEx, HMETAFILEPICT_UserMarshal, CoCopyProxy, ProgIDFromCLSID, RegisterDragDrop, OleRegGetMiscStatus ( 0 exports ) hab jetzt anvenger gestartet, hier das logfile: ////////////////////////////////////////// Avenger Pre-Processor log ////////////////////////////////////////// Platform: Windows XP (build 2600, Service Pack 2) Tue Jun 03 10:52:37 2008 10:52:32: Error: Invalid registry syntax in command: "HKCU\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus" Only registry keys under the HKEY_LOCAL_MACHINE hive are accessible to this program. Skipping line. (Registry value deletion mode) 10:52:37: Error: Execution aborted by user! ////////////////////////////////////////// Logfile of The Avenger Version 2.0, (c) by Swandog46 http://swandog46.geekstogo.com Platform: Windows XP ******************* Script file opened successfully. Script file read successfully. Backups directory opened successfully at C:\Avenger ******************* Beginning to process script file: Rootkit scan active. No rootkits found! Error: file "C:\WINDOWS\system32\scvhost.exe" not found! Deletion of file "C:\WINDOWS\system32\scvhost.exe" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist File "C:\Programme\VAV\vav.exe" deleted successfully. File "C:\WINDOWS\system32\rsrvabru.dll" deleted successfully. File "C:\WINDOWS\system32\csjgitae.dll" deleted successfully. File "C:\Programme\KGB\Mpk.exe" deleted successfully. Error: registry key "\Registry\Machine\System\CurrentControlSet\Services\SomeBadDriver" not found! Deletion of driver "SomeBadDriver" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Error: could not delete registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Mpk.exe" Deletion of registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Mpk.exe" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Error: could not delete registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Windows Update" Deletion of registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Windows Update" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus" deleted successfully. Registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|94d0754d" deleted successfully. Error: could not delete registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus" Deletion of registry value "HKLM\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus" failed! Status: 0xc0000034 (STATUS_OBJECT_NAME_NOT_FOUND) --> the object does not exist Completed script processing. ******************* Finished! Terminate. Geändert von matthias_90 (03.06.2008 um 10:05 Uhr) |
| | #4 |
     | setup.exe blockiert Hi, Du musst bei den Scripten aufpassen, dass sich keine Leerzeichen einschleichen, z. B. "HKLM\Software\Microsoft\Windows\CurrentVersion\Ru n|Mpk.exe" (hier bei Ru n); das bitte korregieren und nochmal durchlaufen lassen (das Löschen der Registry-Keys); Leerzeichen werden im Forum absichtlich "dazwischen" geschoben"... Dann weiter verfahren wie angegeben... chris
__________________  Don't bring me down Don't bring me down Vor dem posten beachten! Spenden (Wer spenden will, kann sich gerne melden  ) ) |
| | #5 |
 | setup.exe blockiert der Registryeintrag "HKCU\Software\Microsoft\Windows\CurrentVersion\Run|Antivirus" funktioniert mit Avenger nicht, nur HKEY_LOCAL_MACHINE Geändert von matthias_90 (03.06.2008 um 11:13 Uhr) |
| | #6 |
     | setup.exe blockiert Hi, ja, isch weis ;o)... Bitte noch fixen mit HJ und combofix.log, sowie AntiMalewareByte... chris
__________________ --> setup.exe blockiert |
 |
| Themen zu setup.exe blockiert |
| antivirus, blockiert, browser, central, compare, desktop, drivers, firefox, google, hijack, hijackthis, home, internet, internet explorer, internet security, ip-adresse, limewire, locker, manuel, mozilla, mozilla firefox, rundll, scan, security, server, software, system, updates, usb, virus, windows, windows xp |